An IT security plan is designed to ensure that an organization's IT systems and data are adequately protected from threats. It should provide a blueprint for developing, implementing, and maintaining an effective IT security strategy that meets the organization's specific needs. The plan should include a risk assessment, identification of security objectives, and a detailed plan for how the organization will meet those objectives.
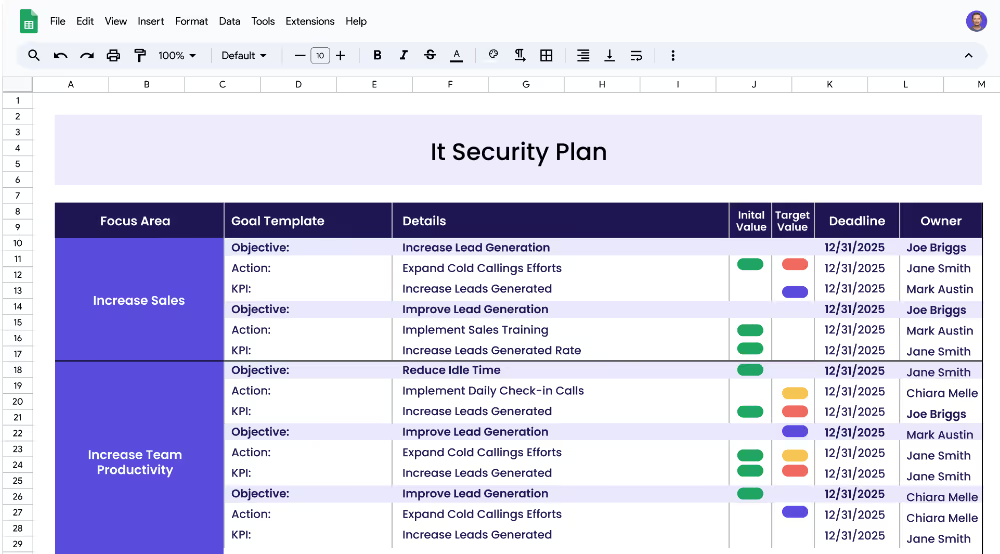
Each focus area has its own objectives, projects, and KPIs to ensure that the strategy is comprehensive and effective.
This IT security plan template is designed for IT leaders, managers, and teams of all sizes and industries who need to create a comprehensive plan to manage their IT security. This template provides a comprehensive framework for developing an IT security plan that addresses the organization’s specific needs and goals.
Focus areas are the major topics that an organization’s IT security plan should address. Examples of focus areas include network security, endpoint security, application security, and data security. Each focus area should include specific objectives and measurable targets (KPIs) that can be used to track progress.
Objectives are specific goals that an organization’s IT security plan should strive to achieve. Examples of objectives include reducing network access vulnerabilities, training employees on security protocols, securing endpoints and devices, and implementing digital rights management.
KPIs (Key Performance Indicators) are measurable targets that can be used to track progress towards an objective. KPIs should be specific, measurable, achievable, relevant, and time-bound. Examples of KPIs include reducing unauthorized access, increasing employee security awareness, increasing endpoint security, and increasing digital rights compliance.
Projects (Actions) are the specific steps that an organization should take to achieve its KPIs. Examples of projects include implementing access control policies, conducting security trainings, deploying endpoint security solutions, and installing digital rights management software.
If you're set to enhance your strategic execution and see quicker results, Cascade Strategy Execution Software presents a robust alternative to traditional spreadsheets. Our platform streamlines the planning, execution, and tracking of your strategies in one centralized, secure, and scalable environment. Increase collaboration, adapt quickly to new security challenges, and maintain strategic alignment across your organization with Cascade's real-time updates and visual dashboards. Sign-up for free or book a demo with one of our strategy experts today!