A cyber security strategy is a plan of action to protect the data and digital assets of an organization. It outlines the policies, procedures and technologies needed to secure networks, systems and data from internal and external threats. This strategy should include the processes and tools used to identify risks, protect against them, detect any security incidents and respond to them in a timely manner.
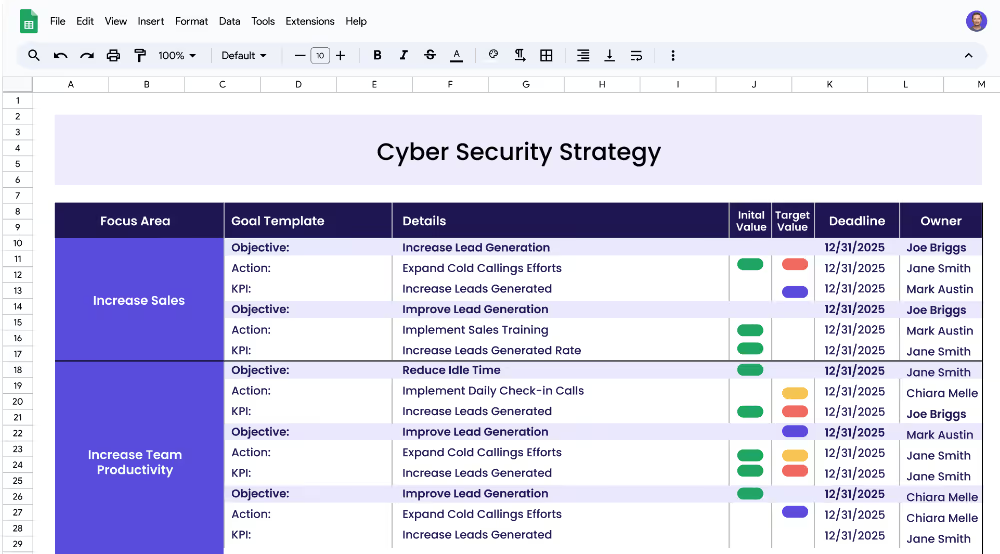
Each focus area has its own objectives, projects, and KPIs to ensure that the strategy is comprehensive and effective.
This cyber security strategy template is for IT security professionals looking to create an effective cyber security strategy. This template provides a framework for you to use to define your focus areas, objectives and key performance indicators (KPIs). It also provides guidance on how to implement projects to achieve the KPIs, and how to use the Cascade Strategy Execution Platform to see faster results from your strategy.
When defining your focus areas, consider the cyber security needs of your organization. Think about the areas that need to be secured and protected from threats, such as cyber security, data privacy, and disaster recovery. Each of these focus areas should have their own objectives and associated KPIs.
Objectives are the goals that you want to achieve for each focus area. For example, for the focus area of cyber security, your objectives could be to implement a comprehensive security system and develop security policies and procedures. For the focus area of data privacy, your objectives could be to implement data privacy measures and protect personal data.
Key performance indicators (KPIs) are measurable targets that you set in order to track your progress towards achieving the objectives. For example, for the objective of implementing a comprehensive security system, you could set a KPI of decreasing security vulnerabilities. For the objective of developing security policies and procedures, you could set a KPI of increasing compliance with security policies.
Projects (or actions) are related tasks or initiatives that are needed to achieve the KPIs. For example, for the KPI of decreasing security vulnerabilities, the project could be to design and implement a comprehensive security system. For the KPI of increasing compliance with security policies, the project could be to create and implement security policies and procedures.
If you're looking to streamline your strategy, Cascade Strategy Execution Software offers a powerful alternative to traditional spreadsheets. With Cascade, you gain access to real-time updates, centralized collaboration, and automated reporting, which significantly enhances your ability to manage and execute sophisticated strategies efficiently and securely. Sign-up for free or book a demo today, and experience a more dynamic and integrated approach to strategy execution.