A security management plan outlines the processes and procedures to protect an organization's data, systems, and networks from malicious or unauthorized access. It includes the steps taken to assess and manage risks, as well as the strategies and policies in place to protect the organization's data and systems. It also outlines the roles and responsibilities of personnel, the technology used to protect the organization's systems, and the process for reporting and responding to security incidents.
Each focus area has its own objectives, projects, and KPIs to ensure that the strategy is comprehensive and effective.
This Security Management Plan template is designed to help IT teams of all sizes and industries create a comprehensive plan for managing their organization's IT security. The template provides a roadmap for establishing objectives, setting KPIs, and implementing projects to achieve those objectives. It is designed to help teams create a plan that is tailored to the specific needs and challenges of their organization.
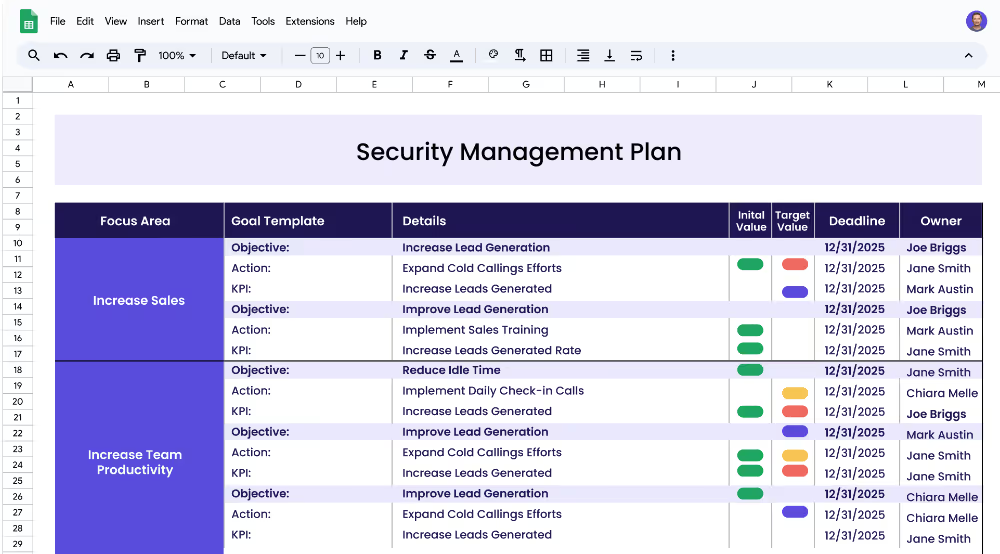
A focus area is a broad category that encompasses a set of related objectives. A Security Management Plan typically includes three main focus areas: Maintain Data Security, Monitor Security Threats, and Manage Security Incidents. Each of these focus areas includes specific objectives and related projects to help organizations address their security challenges.
Objectives are the measurable goals that are set to address the focus area. For example, under the focus area of Maintain Data Security, the objectives could include implementing access control and security protocols. Each objective should be tied to a measurable target, such as increasing user access compliance or decreasing system vulnerability.
KPIs (Key Performance Indicators) are measurable targets that are used to track progress towards achieving the objectives. For example, for the objective of implementing access control, the KPI could be to increase user access compliance. The initial value of the KPI should be set, and a target value should be set to measure the progress towards the objective.
Projects (or actions) are the activities that are necessary to achieve the measurable targets. For example, to achieve the KPI of increasing user access compliance, the project may be to establish roles and user privileges. This project should be linked to the KPI, so that the progress can be tracked.
If you're focused on enhancing your strategic plan swiftly and effectively, Cascade Strategy Execution Software offers a powerful alternative to the tedious spreadsheets. Experience the benefits of real-time updates, centralized collaboration, and visual dashboards which streamline your strategic processes unlike ever before. Sign-up for free or book a demo with one of our strategy experts to see how you can transform the way you secure your organization.